overleaf template galleryLaTeX templates and examples — Recent
Discover LaTeX templates and examples to help with everything from writing a journal article to using a specific LaTeX package.

Template for the submission of contributed talks and posters for the 2024 edition of the autumn meeting of industrial mathematics

Latex Author Kit for BIOSIG 2024 https://biosig.de/

Letter for the University of Alabama at Tuscaloosa
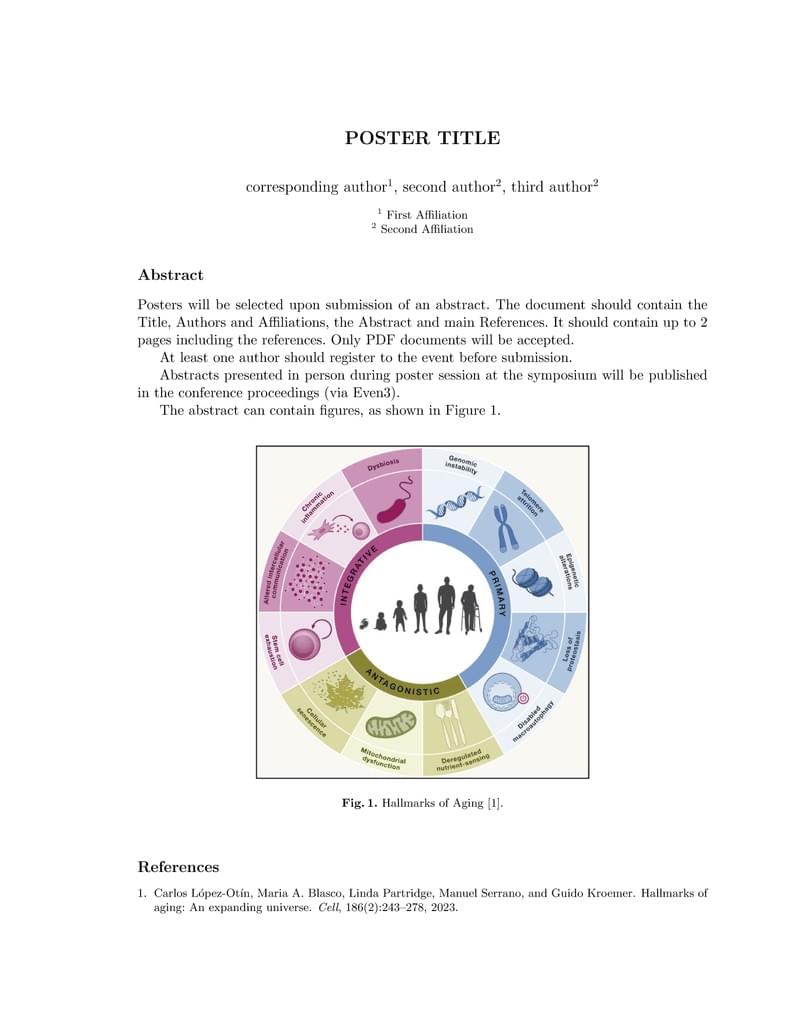
BARTS 2024 abstract submission template.

https://github.com/kai-tub/latex-beamer-pure-minimalistic

Formato de monografia U.D.F.J.D.C.

基于厦门大学模板修改,添加外滩背景和校徽

西安建筑科技大学LaTeX研究生学位论文模版。Github: https://github.com/ChuandongXie/XAUATthesis

Template for the LWDA 2024 conference. https://www.informatik.uni-wuerzburg.de/lwda24/
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.